[New Cisco Dumps] New Updated Cisco 200-105 Dumps ICND2 v3.0 Practice Test Exam Video Online (From Google Drive)
Is that true Cisco 200-105 dumps providing free dumps? “Interconnecting Cisco Networking Devices Part 2 (ICND2 v3.0)” is the name of Cisco 200-105 exam dumps which covers all the knowledge points of the real Cisco exam. New updated Cisco https://www.pass4itsure.com/200-105.html dumps ICND2 v3.0 practice test exam online. Pass4itsure 200-105 dumps exam questions answers are updated (204 Q&As) are verified by experts. The associated certifications of 200-105 dumps is ICND2.
Exam Code: 200-105
Exam Name: Interconnecting Cisco Networking Devices Part 2 (ICND2 v3.0)
Updated: Sep 10, 2017
Q&As: 204
[New Cisco 200-105 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWWWw0QXQxY3R1X1E
[New Cisco 300-320 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWck1GZWpsWHY4ZU0
The List: New Describe Topics for ICND2 200-105 Dumps:
The new ICND2 200-105 exam topics list several conceptual exam topics, all that use the verb describe, as paraphrased below:
1.7.a Describe… 802.1x (was already in the books; just new to the exam topics)
1.7.b Describe DHCP snooping
3.4 Describe WAN topology options
3.5.d Describe DMVPN (Dynamic Multipoint VPN)
4.2 Describe the effects of cloud on enterprise WANs
4.3 Describe QoS concepts
5.5 Describe Network Programmability in an Enterprise network

Pass4itsure Latest and Most Accurate Cisco 200-105 Dumps Exam Q&As:
Question No : 5 – (Topic 1) What is one benefit of PVST+?
A. PVST+ supports Layer 3 load balancing without loops.
B. PVST+ reduces the CPU cycles for all the switches in the network.
C. PVST+ allows the root switch location to be optimized per VLAN.
D. PVST+ automatically selects the root bridge location, to provide optimized bandwidth
usage.
Answer: C
Explanation:
Per VLAN Spanning Tree (PVST)
Introduction
Per VLAN Spanning Tree (PVST) maintains a spanning tree instance for each VLAN configured in the network. This means a switch can be the root bridge of a VLAN while another switch can be the root bridge of other VLANs in a common topology. For example, Switch 1 can be the root bridge for Voice data while Switch 2 can be the root bridge for Video data. If designed correctly, it can optimize the network traffic.
Question No : 6 – (Topic 1)
Refer to the exhibit.
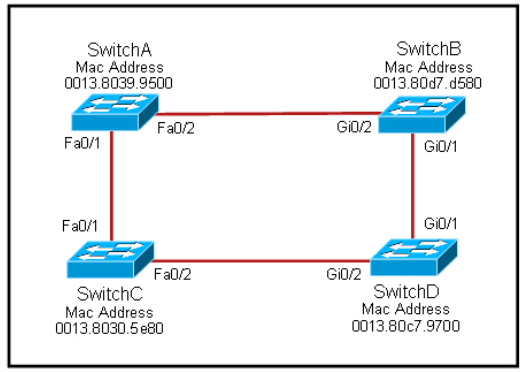
Each of these four switches has been configured with a hostname, as well as being configured to run RSTP. No other configuration changes have been made. Which three of these show the correct RSTP port roles for the indicated switches and interfaces? (Choose three.)
A. SwitchA, Fa0/2, designated
B. SwitchA, Fa0/1, root
C. SwitchB, Gi0/2, root
D. SwitchB, Gi0/1, designated
E. SwitchC, Fa0/2, root
F. SwitchD, Gi0/2, root
Answer: A,B,F
Explanation:
The question says “no other configuration changes have been made” so we can understand these switches have the same bridge priority. SwitchC has lowest MAC address so, it will become root bridge and 2 of its ports (Fa0/1 & Fa0/2) will be designated
ports (DP). Because SwitchC is the root bridge the 2 ports nearest SwitchC on SwitchA (Fa0/1) and SwitchD (Gi0/2) will be root ports (RP) -> B and F are correct. SwitchB must have a root port so which port will it choose? To answer this question we
need to know about STP cost and port cost. In general, “cost” is calculated based on bandwidth of the link. The higher the bandwidth on a link, the lower the value of its cost. Below are the cost values you should memorize: Link speed Cost SwitchB will choose the interface with lower cost to the root bridge as the
root port so we must calculate the cost on interface Gi0/1 & Gi0/2 of SwitchB to the root bridge. This can be calculated from the “cost to the root bridge” of each switch because a switch always advertises its cost to the root bridge in its BPDU. The receiving switch will add its local port cost value to the cost in the BPDU.
SwitchC advertises its cost to the root bridge with a value of 0. Switch D adds 4 (the cost value of 1Gbps link) and advertises this value (4) to SwitchB. SwitchB adds another 4 and learns that it can reach SwitchC via Gi0/1 port with a total cost of 8. The same process happens for SwitchA and SwitchB learns that it can reach SwitchC via Gi0/2 with a total cost of 23 -> Switch B chooses Gi0/1 as its root port. Now our last task is to identify the port roles of the ports between SwitchA & SwitchB. It is rather easy as the MAC address of SwitchA is lower than that of SwitchB so Fa0/2 of
SwitchA will be designated port while Gi0/2 of SwitchB will be alternative port.
Question No : 7 – (Topic 1) Which three of these statements regarding 802.1Q trunking are correct? (Choose three.)
A. 802.1Q native VLAN frames are untagged by default.
B. 802.1Q trunking ports can also be secure ports.
C. 802.1Q trunks can use 10 Mb/s Ethernet interfaces.
D. 802.1Q trunks require full-duplex, point-to-point connectivity.
E. 802.1Q trunks should have native VLANs that are the same at both ends.
Answer: A,C,E
Explanation:
CCNA Self-Study (ICND Exam): Extending Switched Networks with Virtual LANs
Question No : 8 – (Topic 1) Refer to the exhibit.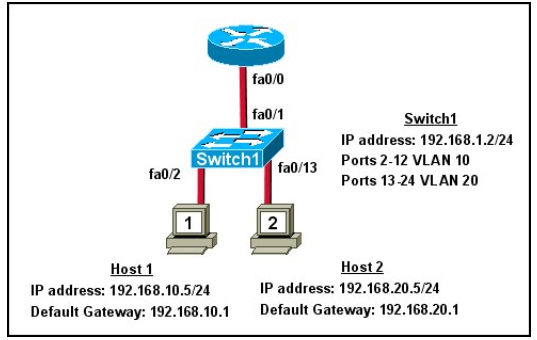
What commands must be configured on the 2950 switch and the router to allow
communication between host 1 and host 2? (Choose two.)
A. Router(config)# interface fastethernet 0/0
Router(config-if)# ip address 192.168.1.1 255.255.255.0
Router(config-if)# no shut down
B. Router(config)# interface fastethernet 0/0
Router(config-if)# no shut down
Router(config)# interface fastethernet 0/0.1
Router(config-subif)# encapsulation dot1q 10
Router(config-subif)# ip address 192.168.10.1 255.255.255.0
Router(config)# interface fastethernet 0/0.2
Router(config-subif)# encapsulation dot1q 20
Router(config-subif)# ip address 192.168.20.1 255.255.255.0
C. Router(config)# router eigrp 100
Router(config-router)# network 192.168.10.0
Router(config-router)# network 192.168.20.0
D. Switch1(config)# vlan database
Switch1(config-vlan)# vtp domain XYZ
Switch1(config-vlan)# vtp server
E. Switch1(config)# interface fastethernet 0/1
Switch1(config-if)# switchport mode trunk
F. Switch1(config)# interface vlan 1
Switch1(config-if)# ip default-gateway 192.168.1.1
Answer: B,E
Explanation:
The two answers B and E list all the commands needed to configure interVLAN routing. Please notice that Cisco switch 2950, 2960 only support dot1Q trunking so we don’t need to specify which trunking encapsulation to use in this case. For Cisco switches 3550 or above we have to use these commands instead:
Switch3550(config-if)#switchport trunk encapsulation dot1q Switch3550(config-if)#switchport mode trunk
Question No : 9 – (Topic 1) Which two of these statements regarding RSTP are correct? (Choose two.)
A. RSTP cannot operate with PVST+.
B. RSTP defines new port roles.
C. RSTP defines no new port states.
D. RSTP is a proprietary implementation of IEEE 802.1D STP.
E. RSTP is compatible with the original IEEE 802.1D STP.
Answer: B,E
Explanation:
Port Roles
The role is now a variable assigned to a given port. The root port and designated port roles remain, while the blocking port role is split into the backup and alternate port roles. The Spanning Tree Algorithm (STA) determines the role of a port based on Bridge Protocol Data Units (BPDUs). In order to simplify matters, the thing to remember about a BPDU is there is always a method to compare any two of them and decide whether one is more
useful than the other. This is based on the value stored in the BPDU and occasionally on the port on which they are received. This considered, the information in this section explains practical approaches to port roles. Compatibility with 802.1D RSTP is able to interoperate with legacy STP protocols. However, it is important to note that the inherent fast convergence benefits of 802.1w are lost when it interacts with legacy bridges.
QUESTION NO: 9
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2008 as its
application development platform. You create an ASP.NET Web application using .NET
Framework 3.5. You create a Web form in the application that permits users to provide personal
information. You add a DropDownList control to the Web form to retrieve the residential status of
users. The default item that the DropDownList control displays is the “Select Country” option. You
have to ensure that users select a country other than the default option. Which of the following
validation controls should you use to accomplish this task?
A. RangeValidator
B. RequiredFieldValidator
C. CustomValidator
D. RegularExpressionValidator
Answer: B
QUESTION NO: 10
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its
application development platform. You create an application for the company. You need to
validate the phone number passed to a class as a parameter in the application. Which of the
following is the most effective way to verify that the format of the data matches a phone number?
A. Regular expressions
B. Nested If statements
C. Use the String.Length property
D. A try/catch block
Answer: A
QUESTION NO: 11
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET 2005 as its
application development platform. You have recently finished development of a Windows
application using .NET Framework. Users report that the application is not running properly. When
the users try to complete a particular action, the following error message comes out:
Unable to find assembly ‘myservices, Version=1.0.0.0, Culture=neutral,
PublicKeyToken=29b5ad26c9de9b95′.
You notice that the error occurs as soon as the application tries to call functionality in a serviced
component that was registered by using the following command:
regsvcs.exe myservices.dll
You must make sure that the application can call the functionality in the serviced component with
no exceptions being thrown. What will you do to accomplish this task?
A. Run the command line tool: regasm.exe myservices.dll.
B. Copy the serviced component assembly into the C:\Program Files\ComPlus Applications folder.
C. Run the command line tool: gacutil.exe /i myservices.dll.
D. Copy the serviced component assembly into the C:\WINDOWS\system32\Com folder.
Answer: C
QUESTION NO: 12
Allen works as a Software Developer for ABC Inc. The company uses Visual Studio.NET as its
application development platform. He creates an application using .NET Framework. He wants to
encrypt all his e-mails that he sends to anyone. Which of the following will he use to accomplish
the task?
A. PPP
B. FTP
C. PPTP
D. PGP
Answer: D
QUESTION NO: 13
You work as a Software Developer for ABC Inc. The company has several branches worldwide. The company uses Visual Studio.NET 2005 as its application development platform. You have recently finished the development of an application using .NET Framework 2.0. The application can be used only for cryptography. Therefore, you have implemented the application on a computer. What will you call the computer that implemented cryptography?
A. Cryptographic toolkit
B. Cryptosystem
C. Cryptographer
D. Cryptanalyst
Answer: B
QUESTION NO: 14
You work as a Software Developer for ABC Inc. The company uses Visual Studio .NET as its application development platform. You create a class library using the .NET Framework. The library will be used to open the NSCs of computers. Later, you will set up the class library to the GAC and provide it Full Trust permission. You write down the following code segments for the socket connections: SocketPermission permission = new SocketPermission(PermissionState.Unrestricted);
permission.Assert();
A number of the applications that use the class library may not have the necessary permissions to
open the network socket connections. Therefore, you are required to withdraw the assertion.
Which of the following code segments will you use to accomplish the task?
A. permission.PermitOnly();
B. CodeAccessPermission.RevertDeny();
C. permission.Deny();
D. CodeAccessPermission.RevertAssert();
E. permission.Demand();
Answer: D
QUESTION NO: 15
You work as an Application Developer for ABC Inc. You are assigned with developing a Web site that will handle information related to monthly sales of the company. You wish to secure the Web site so that only employees of the Accounts department can view the Web pages. You need to create roles for the employees of this department. The user account information will be stored in a
SQL Server database named Database. You decide to do all this by using the Web Site Administration Tool. Which of the following types of security will you use to accomplish the task?
A. Forms-based authentication
B. Integrated Microsoft Windows authentication
C. Basic authentication
D. Digest authentication
Answer: A
The country in which a person lives don’t matter, individuals living in any corner of the world can get the Cisco 200-105 dumps as there is only a requirement of having an internet connection through which a person can download https://www.pass4itsure.com/200-105.html dumps questions.
