312-50V12 DUMPS 2023 | Effective preparation strategy

EC-COUNCIL 312-50V12 The exam is very popular and has many suitors. How to prepare it effectively? Candidates need to know about the 312-50v12 exam and be familiar with the mode. This is important for cracking the exam. At this time, 312-50V12 dumps 2023 appear.
Exams require adequate practice and preparation. Pass4itSure provides an effective preparation strategy that is strategic and well-planned to ensure success. Its updated 312-50V12 dumps 2023 https://www.pass4itsure.com/312-50v12.html is the best helper for cracking the exam.
About 312-50V12 exam
As mentioned earlier, the 312-50v12 exam mode is important. Familiarize yourself with question types, scores, the importance of content proportions, and time.
You can find it in Certified Ethical Hacker v12 Certification Get these basics on the official CEH v12 website.
The URL link is as follows:
https://www.eccouncil.org/train-certify/certified-ethical-hacker-ceh/
https://www.eccouncil.org/certified-ethical-hacker-training-and-certification/
Using a Pass4itSure 312-50v12 dumps
312-50v12 dumps 2023 not only provides you with the latest exam questions, but another important role is also to improve and practice the exam. This helps to analyze weak areas and better focus on them. At the same time, you can also learn to manage your time effectively. It also gives you confidence.
This also answers the question of why it is an effective preparation strategy.
Try the EC-Council 312-50v12 free dumps (2023) demo below:
Question 1:
A friend of yours tells you that he downloaded and executed a file that was sent to him by a coworker. Since the file did nothing when executed, he asks you for help because he suspects that he may have installed a trojan on his computer.
what tests would you perform to determine whether his computer Is Infected?
A. Use ExifTool and check for malicious content.
B. You do not check; rather, you immediately restore a previous snapshot of the operating system.
C. Upload the file to VirusTotal.
D. Use netstat and check for outgoing connections to strange IP addresses or domains.
Correct Answer: D
Question 2:
Identify the UDP port that Network Time Protocol (NTP) uses as its primary means of communication.
A. 113
B. 69
C. 123
D. 161
Correct Answer: C
https://en.wikipedia.org/wiki/Network_Time_Protocol The Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks. NTP is intended to synchronize all participating computers within a few milliseconds of Coordinated Universal Time (UTC).
It uses the intersection algorithm, a modified version of Marzullo\’s algorithm, to select accurate time servers and is designed to mitigate variable network latency effects. NTP can usually maintain time to within tens of milliseconds over the public Internet and achieve better than one-millisecond accuracy in local area networks.
Asymmetric routes and network congestion can cause errors of 100 ms or more. The protocol is usually described in terms of a client-server model but can easily be used in peer-to-peer relationships where both peers consider the other to be a potential time source.
Implementations send and receive timestamps using the User Datagram Protocol (UDP) on port number 123.
Question 3:
Leverox Solutions hired Arnold, a security professional, for the threat intelligence process. Arnold collected information about specific threats against the organization. From this information, he retrieved contextual information about security events and incidents that helped him disclose potential risks and gain insight into attacker methodologies. He collected the information from sources such as humans, social media, and chat rooms as well as from events that resulted in cyberattacks. In this process, he also prepared a report that includes identified malicious activities, recommended courses of action, and warnings for emerging attacks. What is the type of threat intelligence collected by Arnold in the above scenario?
A. Strategic threat intelligence
B. Tactical threat intelligence
C. Operational threat intelligence
D. Technical threat intelligence
Correct Answer: C
Question 4:
A company\’s security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?
A. Attempts by attackers to access the user and password information stored in the company\’s SQL database.
B. Attempts by attackers to access Web sites that trust the Web browser user by stealing the user\’s authentication credentials.
C. Attempts by attackers to access passwords stored on the user\’s computer without the user\’s knowledge.
D. Attempts by attackers to determine the user\’s Web browser usage patterns, including when sites were visited and for how long.
Correct Answer: B
Question 5:
Morris, a professional hacker, performed a vulnerability scan on a target organization by sniffing the traffic on the network to identify the active systems, network services, applications, and vulnerabilities.
He also obtained the list of the users who are currently accessing the network. What is the type of vulnerability assessment that Morris performed on the target organization?
A. internal assessment
B. Passive assessment
C. External assessment
D. Credentialed assessment
Correct Answer: B
Passive Assessment Passive assessments sniff the traffic present on the network to identify the active systems, network services, applications, and vulnerabilities. Passive assessments also provide a list of the users who are currently accessing the network.
Question 6:
What is the following command used for?
net use \targetipc$ “/u:” A. Grabbing the etc/passwd file
B. Grabbing the SAM
C. Connecting to a Linux computer through Samba.
D. This command is used to connect as a null session
E. Enumeration of Cisco routers
Correct Answer: D
Question 7:
Which of the following is the least-likely physical characteristic to be used in biometric control that supports a large company?
A. Iris patterns
B. Voice
C. Height and Weight
D. Fingerprints
Correct Answer: C
Question 8:
What piece of hardware on a computer\’s motherboard generates encryption keys and only releases a part of the key so that decrypting a disk on a new piece of hardware is not possible?
A. CPU
B. GPU
C. UEFI
D. TPM
Correct Answer: D
The TPM is a chip that\’s part of your computer\’s motherboard — if you bought an off-the-shelf PC, it\’s soldered onto the motherboard.
If you built your own computer, you can buy one as an add-on module if your motherboard supports it. The TPM generates encryption keys, keeping part of the key to itself.
Question 9:
What is the least important information when you analyze a public IP address in a security alert?
A. DNS
B. Whois
C. Geolocation
D. ARP
Correct Answer: D
Question 10:
Steven connected his iPhone to a public computer that had been infected by Clark, an attacker. After establishing the connection with the public computer, Steven enabled iTunes WI-FI sync on the computer so that the device could continue communication with that computer even after being physically disconnected.
Now, Clark gains access to Steven\’s iPhone through the infected computer and is able to monitor and read all of Steven\’s activity on the iPhone, even after the device is out of the communication zone.
Which of the following attacks is performed by Clark in the above scenario?
A. IOS trustjacking
B. lOS Jailbreaking
C. Exploiting SS7 vulnerability
D. Man-in-the-disk attack
Correct Answer: A
An iPhone client\’s most noticeably terrible bad dream is to have somebody oversee his/her gadget, including the capacity to record and control all actions without waiting to be in a similar room.
In this blog entry, we present another weakness called “Trustjacking”, which permits an aggressor to do precisely that. This weakness misuses an iOS highlight called iTunes Wi-Fi sync, which permits a client to deal with their iOS gadget without genuinely interfacing it with their PC.
A solitary tap by the iOS gadget proprietor when the two are associated with a similar organization permits an assailant to oversee the gadget. Furthermore, we will stroll through past related weaknesses and show the progressions that iPhone has made to alleviate them, and why these are adequate not to forestall comparative assaults.
After interfacing an iOS gadget with another PC, the clients are found out if they trust the associated PC or not. Deciding to believe the PC permits it to speak with the iOS gadget by means of the standard iTunes APIs.
This permits the PC to get to the photographs on the gadget, perform reinforcement, introduce applications, and considerably more, without requiring another affirmation from the client and with no recognizable sign.
Besides, this permits enacting the “iTunes Wi-Fi sync” highlight, which makes it conceivable to proceed with this sort of correspondence with the gadget even after it has been detached from the PC, as long as the PC and the iOS gadget are associated with a similar organization.
It is intriguing to take note that empowering “iTunes Wi-Fi sync” doesn’t need the casualty\’s endorsement and can be directed simply from the PC side. Getting a live stream of the gadget\’s screen should be possible effectively by consistently requesting screen captures and showing or recording them distantly.
It is imperative to take note that other than the underlying single purpose of disappointment, approving the vindictive PC, there is no other component that forestalls this proceeding with access.
Likewise, there isn’t anything that informs the clients that by approving the PC they permit admittance to their gadget even in the wake of detaching the USB link.
Question 11:
Sam, is a professional hacker. targeted an organization with intention of compromising AWS IAM credentials. He attempted to lure one of the employees of the organization by initiating fake calls while posing as a legitimate employee.
Moreover, he sent phishing emails to steal the AWS 1 AM credentials and further compromise the employee\’s account. What is the technique used by Sam to compromise the AWS IAM credentials?
A. Social engineering
B. insider threat
C. Password reuse
D. Reverse engineering
Correct Answer: A
Just like any other service that accepts usernames and passwords for logging in, AWS users are vulnerable to social engineering attacks from attackers. fake emails, calls, or any other method of social engineering, may find yourself with AWS users\’ credentials within the hands of an attacker.
If a user only uses API keys for accessing AWS, general phishing techniques could still use to gain access to other accounts or their pc itself, where the attacker may then pull the API keys for the aforementioned AWS user. With basic open-source intelligence (OSINT), it\’s usually simple to collect a list of workers of an organization that uses AWS on a regular basis.
This list will then be targeted with spear phishing to do and gather credentials. an easy technique may include an email that says your bill has spiked 500th within the past 24 hours, “click here for additional information”, and when they click the link, they\’re forwarded to a malicious copy of the AWS login page designed to steal their credentials.
An example of such an email will be seen in the screenshot below. it\’s exactly like an email that AWS would send to you if you were to exceed the free tier limits, except for a few little changes.
If you clicked on any of the highlighted regions within the screenshot, you\’d not be taken to the official AWS website and you\’d instead be forwarded to a pretend login page setup to steal your credentials.
These emails will get even more specific by playing a touch bit of additional OSINT before causing them out. If an attacker was ready to discover your AWS account ID online somewhere, they could use methods we at rhino have free previously to enumerate what users and roles exist in your account with no logs of contact on your side.
they could use this list to refine their target list, further as their emails to reference services they will know that you often use.
For reference, the journal post for using AWS account IDs for role enumeration will be found here and the journal post for using AWS account IDs for user enumeration will be found here.
During engagements at the rhino, we find that phishing is one of the fastest ways for us to achieve access to an AWS environment.
Question 12:
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server model in the application she is working on. She utilizes a component that can process API requests and handle various Docker objects, such as containers, and volumes. Images, and networks.
What is the component of the Docker architecture used by Annie in the above scenario?
A. Docker client
B. Docker objects
C. Docker daemon
D. Docker registries
Correct Answer: C
Docker uses a client-server design. The docker client talks to the docker daemon, which will do the work of building, running, and distributing your Docker containers. The docker client and daemon will run on the same system, otherwise, you will connect a docker consumer to a remote docker daemon.
The docker consumer and daemon communicate using a REST API, over OS sockets or a network interface.
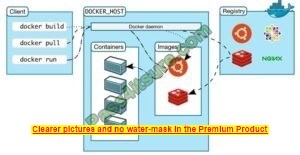
The docker daemon (docked) listens for docker API requests and manages docker objects like pictures, containers, networks, and volumes. A daemon may communicate with other daemons to manage docker services.
Question 13:
When configuring wireless on his home router, Javik disables SSID broadcast. He leaves authentication “open” but sets the SSID to a 32-character string of random letters and numbers.
What is an accurate assessment of this scenario from a security perspective?
A. Since the SSID is required in order to connect, the 32-character string is sufficient to prevent brute-force attacks.
B. Disabling SSID broadcast prevents 802.11 beacons from being transmitted from the access point, resulting in a valid setup leveraging “security through obscurity”.
C. It is still possible for a hacker to connect to the network after sniffing the SSID from a successful wireless association.
D. Javik\’s router is still vulnerable to wireless hacking attempts because the SSID broadcast setting can be enabled using a specially crafted packet sent to the hardware address of the access point.
Correct Answer: C
Question 14:
Security administrator John Smith has noticed abnormal amounts of traffic coming from local computers at night. Upon review, he finds that user data have been exfiltrated by an attacker.
AV tools are unable to find any malicious software, and the IDS/IPS has not reported on any non-whitelisted programs, what type of malware did the attacker use to bypass the company\’s application whitelisting?
A. Phishing malware
B. Zero-day malware
C. File-less malware
D. Logic bomb malware
Correct Answer: C
https://www.mcafee.com/enterprise/en-us/security-awareness/ransomware/what-is-fileless-malware.html
Question 15:
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
A. USER, NICK
B. LOGIN, NICK
C. USER, PASS
D. LOGIN, USER
Correct Answer: A
The above is just to share some of the exam practice questions, complete need to get the latest 312-50V12 dumps https://www.pass4itsure.com/312-50v12.html (total 528 questions).
Conclusion:
The 312-50V12 exam is related to the Certified Ethical Hacker Exam (CEHv12) certification. Therefore, it is a huge help for those who pass smoothly. So, if you plan to move to the next level of your career, using 312-50v12 dumps 2023 as an effective preparation strategy to get through it, is essential.
